Your business has been breached and sensitive data stolen. Now what? Well, now you start working on damage control. There will be financial implications, but that’s nothing compared to the risk of losing customer or investor trust.
The “good” news is consumers and stakeholders are increasingly accepting the inevitability of breaches. Almost half the American population has had their information compromised in a breach.
Consequently, the court of public opinion is now more concerned about how businesses respond to the breach than the fact that it occurred.
This is where crisis PR comes in.
How you communicate will shape customer loyalty, investor confidence, and media perception immediately after the breach and long after it has happened. Any miscalculation in your tone, timing, transparency, and follow-through can have lasting implications.
Follow along as we explore the critical role of public relations in reputation management after a data breach. We will cover:
- The key elements of successful crisis PR communication
- How to get messaging right from the start
- How to rebuild trust over the long term
We’ll draw lessons from real-world breaches including Equifax, Yahoo, T-Mobile, and LastPass to highlight what went wrong, what worked, and what you can do differently.
Understanding the reputational consequences of a data breach
Perhaps no company illustrates the lasting reputational implications of a data breach than Equifax. It’s been almost a decade since the infamous breach, but mentioning the company name still evokes mistrust.
It wasn’t just one of the largest breaches in U.S. history (over 147 million people were affected); it was also one of the most poorly handled. And the first mistake the company made was delayed disclosure. It took over a month for the company to notify the public.
Their second blunder was in their initial statement, which was perceived as lacking accountability and empathy.
Equifax initially offered free credit monitoring to affected consumers, but with a catch. They had to waive their right to sue the company. The company later retracted the statement and the CEO apologized, but the damage was already done.
Eventually, Equifax had to undergo complete leadership restructuring and implement a list of enhanced security measures to regain public trust.
The downfall of Yahoo
Yahoo is another great example of how delayed disclosure can have enduring implications for brand reputation. In 2013, the company suffered what was the biggest breach ever at the time, exposing the customer data of all its 3 billion users. It was not until 2016 that the company disclosed the breach, together with another one that had happened in 2014 affecting 500 million users.
There was no coming back from the reputational damage. The only reason Yahoo exists today is because it pivoted to media, giving way to Google as the dominant email provider.
Key lessons: There are three key elements to a successful post-breach PR strategy: speed, transparency, and accountability. Delays in disclosure, withholding critical information, and a lack of accountability are recipes for disaster. Both Equifax and Yahoo learned this a bit too late.
The golden hours: First 24-48 hours post breach
What you say (or don’t say) in this time window will set the tone for how the public, media, and your stakeholders perceive you.
Admittedly, data breaches present a unique challenge compared to many other crises. This is because not all the facts are immediately clear. On average, organizations can take 204 days to identify a data breach and 73 days to contain it.
However, staying silent while you work out the details is never the right choice. Well, unless it was the company that discovered the breach and has already notified affected customers and relevant stakeholders. If news of the breach are already out there, say the hackers published the data on the dark web, you need to respond immediately.
Failure to comment on the issue will create an “information vacuum,” leaving room for speculation and misinformation. It also makes you vulnerable to opportunistic attacks from competitors, highlighting their own security measures.
Pro tip: If a data breach has caught you unprepared, don’t improvise. Call in external experts including Crisis PR professionals, forensics teams, and legal advisors who can help you strategically navigate the breach.
Developing a comprehensive communication strategy
That initial shock after you’ve been notified that the company has been breached, snap out of it and get to work immediately.
Step 1: Assemble the avengers
A bit dramatic, but the first step should be bringing together the internal or external team that will be executing the post-breach reputation management. The communication, legal, and security teams need to be fully aligned.
The challenge? Legal wants to avoid liability. The security team doesn’t want to look incompetent. Yet, the initial messaging needs to demonstrate empathy and accountability.
The secret? Don’t let them dictate the words. Listen to their perspectives and then craft statements that acknowledge responsibility without overexposing the company.
Step 2: Identify key stakeholders
All stakeholders from the customers to investors, regulators, partners, and the media have a different stake in the breach. Your messaging must reflect that. You also need to prioritize them based on level of urgency. Who do we notify first?
That said, make sure internal communication is aligned before going external. Without proper guidance, employees can say the wrong thing while interacting with customers and other stakeholders. The last thing you need while mitigating a data breach is contradicting messages.
Step 3: Choosing the right communication channel
Depending on the attack type, your standard communication channels may be unavailable. For instance, ransomware can lock you out of your systems such that even accessing your customer contact information is impossible. What’s your fallback? It’s in such cases that social media becomes indispensable.
This is also where having secure, cloud-based platforms in place helps. Many SaaS tools offer built-in backups, team messaging, and automated alerts that keep your team aligned—even during major disruptions.
Step 4: Designate a credible spokesperson
It’s best for the company’s image when a high-ranking official like the CEO or even the CISO becomes the voice of the breach. But sometimes, they’re too caught up in the operational aspects of restoring normalcy to have time to respond to incoming queries. Also, these executives have little media training in most cases and may unknowingly make matters worse with their statements.
Your best bet in this case is a communications lead who can strike the right balance between technical clarity and public reassurance.
Depending on the situation, you might also need to record a video message or live stream a statement to address widespread concerns quickly and directly—especially if written updates aren’t sufficient to reassure stakeholders.
Managing the media and external communication
In the hours and days following a data breach, the media becomes your biggest risk and your best opportunity. See, managing public perception isn’t just about releasing statements. It’s about shaping the story before someone else does it for you. That starts with active media monitoring.
Journalists, security researchers, and tech influencers will begin speculating about the breach almost immediately. If you’re not paying attention to what’s being said, you’ll always be one step behind. Monitoring tools and alerts can help you track evolving narratives, flag misinformation, and respond before rumors harden into facts. Internally, using a centralized ticketing system can streamline incoming inquiries and ensure that all customer communications are tracked, prioritized, and resolved efficiently during the crisis.
Reactive vs proactive reputation management
While you will undoubtedly need to respond to media inquiries (reactive), a well-executed strategy also involves proactively pushing accurate information and your organization’s narrative.
This can include issuing press releases with factual updates, offering expert spokespeople for interviews, and publishing blog posts or statements directly addressing key concerns. As shown by Nextiva’s digital care strategy, engaging customers before they complain, like sending personalized updates, using social listening tools, or flagging issues based on account activity, can go a long way in preserving your brand’s reputation.
Proactive communication allows you to own the story, rather than solely playing defense against negative reporting.
Make strategic relationships with reporters
It’s also vital to recognize the significant role played by cybersecurity trade publications, blogs, and independent security researchers. These entities are often considered Subject Matter Experts (SMEs) within the cybersecurity community.
Their analyses and opinions frequently carry significant weight and can significantly influence the narrative adopted by local and national news outlets.
Building relationships with key security journalists and researchers and engaging with them respectfully and transparently can help ensure that their reporting is based on facts rather than speculation.
Mistakes to avoid in your communication
1. Neglecting core crisis principles
Speed, transparency, and accountability. Make sure your communication ticks all three. When T-Mobile experienced a breach in 2021 affecting 54 million people, it moved fast. But its tone missed the mark.
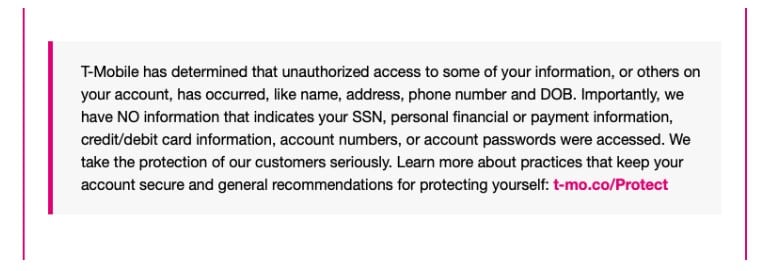
The SMS lacked empathy and accountability. It also minimized the breach. The exposed data, name+phone number+address+dob, was enough for identity theft and targeted phishing.
A better approach would have been to own the facts, express regret, and show action:
“We’re writing to inform you that some information from your T-Mobile account, like name, address, phone number, and date of birth, was accessed without authorization. We want to be clear: your Social Security number, financial details, and account passwords were not affected. We’re truly sorry this happened. We know how important your privacy is, and we take this breach seriously. We’re already taking steps to enhance our systems and prevent future incidents.”
2. Releasing premature technical claims
When the full scope of a breach is unknown, initial statements should be carefully crafted to avoid making definitive claims that may later prove false. It is better to communicate uncertainty with a commitment to ongoing updates than to issue premature reassurances that need to be retracted later.
Popular password management company, LastPass, learned this the hard way when it was breached in 2022. The company had initially claimed that no customer data was compromised and that the attack was mitigated. However, there was a subsequent attack in which hackers got away with encrypted customer vault data. Further reports revealed that the hackers decrypted the vaults of some customers and used stored passwords to steal millions in cryptocurrency.
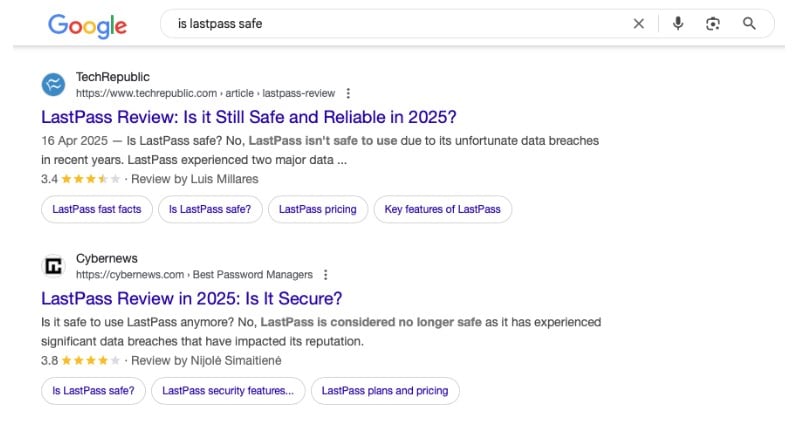
The result was a mass exodus of customers and a tarnished reputation that the company has not recovered from.
Communication tip: Avoid discussing specific technical vulnerabilities, details about ransom demands, speculation about attackers, or unconfirmed impacts in initial statements. These can create additional risks or lead to damaging retractions. Instead, confirm awareness of the incident, express concern, and commit to updates as you receive them.
Rebuilding customer trust and brand reputation
Good news, you’ve survived the headlines. However, there are still lingering concerns from your immediate stakeholders. To rebuild their trust you’ll need to demonstrate a genuine commitment to security, transparency, and customer well-being over the long term.
Some tips to apply on your road to recovery:
- Offer recovery benefits to affected individuals: If customers have suffered financial losses from the breach, offer financial compensation. Add identity theft protection and credit monitoring for all affected individuals to prevent further attacks.
- Share lessons learned from the incident and detail new security enhancements: Once bitten, twice shy. The truth is, breaches can happen to anyone. It’s better that it happened to you because you’re now more prepared for new attacks.
- Third-party validation: This can include certifications, security firm assessments, or endorsements from industry regulators. When neutral experts vouch for your progress, it helps repair the trust you lost, especially among partners and enterprise customers.
While at it, continue monitoring public sentiment through surveys, social listening, and media analysis to gauge recovery. Are people still bringing up the breach in conversations about your brand? Address it.
You may have to develop a campaign dedicated to rebuilding customer trust or, in the worst-case scenario, rebranding to signal a new chapter and find new leads.
Measuring PR response
How do you know if your crisis PR communication is working? You need to define and track relevant metrics.
Key measures include:
- Media coverage and sentiment: Use monitoring tools to count the number of news stories and social mentions your breach gets, and whether they are positive or negative. Additionally, tracking the share of voice (your company vs others in the news) shows if coverage is escalating. Are headlines focusing on your apology and fixes or your failures?
- Web and social engagement metrics: Website analytics can also be a good measure of recovery. For example, a spike in visits to your incident FAQ or newsroom means people are seeking answers. This is great as long as your content is helpful. Also, note how many people click through to the credit monitoring signup or hotline. Social media engagement (likes, shares, comments) can be a proxy for audience sentiment as well.
- Customer response and business impact: Track business indicators like customer churn, support call volume, and sales trends. If possible, conduct quick surveys or check customer sentiment indexes. For instance, after Equifax’s breach, surveys showed a measurable drop in trust. In a corporate context, monitor client inquiries or cancellations. The finance side is also a metric. An increasing number of refunds and settlements means you still have work to do.
Don’t overlook your call center activity, either. According to GetVoIP, monitoring customer calls can help detect early signs of dissatisfaction, such as long hold times and repeated complaints, which are often precursors to churn. Real-time call monitoring allows managers to intervene before issues escalate, protecting customer relationships during sensitive periods like post-crisis recovery.
Remember, it won’t happen in weeks or even months. But with the right actions and consistent messaging, the breach can become part of your brand’s resilience story.
Proactive measures for future preparedness
Effectively managing the aftermath of a data breach is critical, but your priority should be pre-breach initiatives. Investing in preparedness reduces the likelihood of a breach and significantly enhances your organization’s ability to respond swiftly and effectively if one does happen.
How you do that is by having a comprehensive Incident Response Plan (IRP) that’s regularly updated. An IRP removes guesswork from post-breach response by clearly outlining:
- Roles and responsibilities of the avengers
- Communication protocols (both internal and external)
- Escalation procedures
- Data breach containment strategies
- Forensic investigation steps
- Legal notification requirements.
It’s recommended that the company go through the IRP at least annually or after an incident affecting your industry to ensure it still holds. “There’s nothing worse than pulling that (IRP) off the shelf to find that all the details contained within it are out of date,” Tom Bolitho, senior director of cyber and crisis communications, FTI Consulting.
Additionally, tabletop exercises are a great way to refine incident response plans. These involve simulating different breach scenarios and having the responders show their preparedness.
Also, consider getting cyber insurance. While it won’t help with reputation management, you’ll have peace of mind knowing you’re cautioned against a big chunk of the resulting financial costs. Many businesses have closed shop in the aftermath of breaches because they no longer had the finances to sustain operations.
Conclusion
It’s not the end of the road just because you suffered a breach. And with all the information provided in this post, you have the exact roadmap to prevent your business from being another cautionary tale. Of course, you need to ensure security is solid in the events leading up to a breach.
Your rebuilding will be significantly harder if the breach was the result of glaring negligence. Still, the approach remains the same: fast acknowledgement, transparent disclosure, and a readiness to do better.
You’ll benefit immensely from having an incident response plan in place, but if that’s not the case, seek external help. It’s better to incur the additional cost than suffer irreversible reputation damage.



