As brands and businesses struggle to win digital trust, it’s no surprise that this goal remains so elusive when you consider the continued escalation of cybersecurity shortfalls—new research from risk management firm Prevalent reveals that well over half (61 percent) of companies experienced a third-party data breach or cybersecurity incident last year. In all, breaches rose 20 points—or 49 percent—year over year, increasing threefold since 2021. Is there a solution in sight?
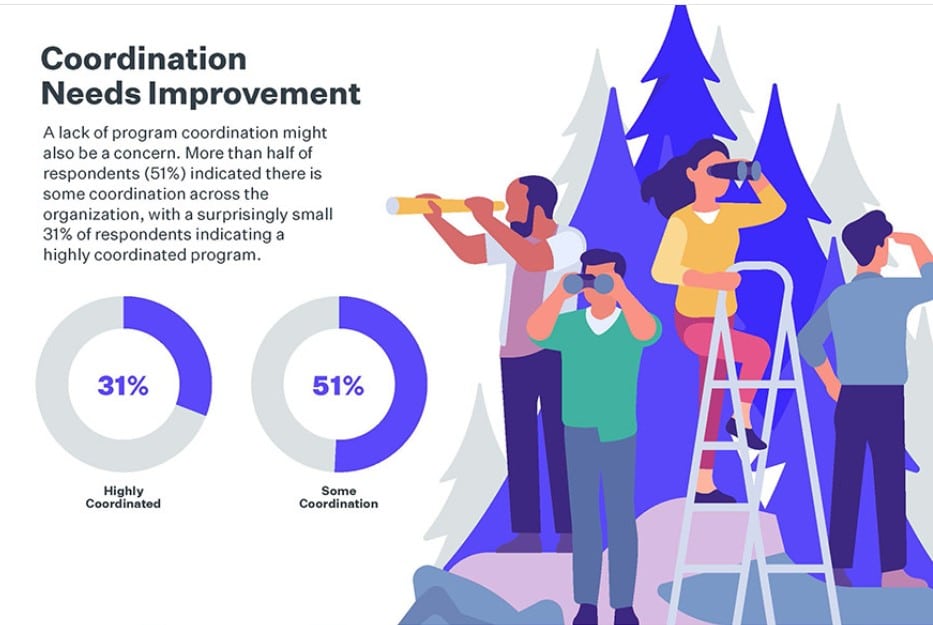
The firm’s 2024 Third-Party Risk Management (TPRM) study identifies multiple areas of concern that could explain the unprecedented breadth and depth of third-party breaches—primarily companies’ reliance on multiple tools to manage data systems, which represents a careless lack of coordination that leaves their supply chains unguarded—and this supply-chain exposure creates a cascading wave of data vulnerability. Only a third of respondents indicated their third-party security programs were highly coordinated.
“What stands out in our report isn’t only the number of breaches, which is the highest we’ve tracked, but also the scale,” said Prevalent CEO Kevin Hickey, in a news release. “Breaches in 2023 impacted huge supply chains—from Okta and LastPass to Change Healthcare and PJ&A—exposing sensitive records of millions of people worldwide. There has never been a more urgent time to take third-party security more seriously.”
“Although most organizations report having TPRM programs in place, half still rely on spreadsheets and use a patchwork of tools to assess their vendors,” said Prevalent COO Brad Hibbert in the release, adding that 60 percent of respondents are not using a dedicated TPRM platform.
While the survey respondents’ average number of third parties was 3,200, respondents reported assessing or monitoring only 33 percent of those vendors. “There is a lot of risk hiding among those unassessed relationships,” said Hibbert.
More than 62 percent of respondents reported understaffing was the biggest obstacle to better safeguarding their organizations from third-party breaches. The average respondent said they need double their current staff dedicated to third-party security.
“Later stages of third-party lifecycles lack adequate risk assessment and monitoring, and overall remediation is woefully lacking,” according to the report. While nearly 90 percent of companies track risks from the sourcing and selection phases, fewer than 80 percent track service-level agreements (SLAs) and offboarding risks later in the relationship lifecycle.
“What surprised us was the disparity between the share of organizations tracking risks and the share remediating them,” explained Hibbert. “A shockingly low 46 percent of companies report remediating risk as a result of risk assessments—the stage where risks must be mitigated.”
The researchers found that AI use remains low in the sector, with only 5 percent of companies actively leveraging AI in their TPRM programs. However, interest remains high, with 61 percent saying they are actively investigating its uses.
The firm advises creating cross-functional teams and establishing clear ownership of TPRM programs as well as automating TPRM processes around a single platform to unify teams, data, and risk lifecycles.
Download the full report here.
Conducted this February and March, the survey’s respondents include heads of information security, data privacy, risk management, procurement, and other IT executives at companies spanning dozens of industries and whose supply chains collectively represent half a million vendors.